Protect Your Cloud Infrastructure
Misconfigured clouds are breaches waiting to happen. We implement enterprise-grade security controls, monitoring, and compliance frameworks—so your business stays safe without slowing down.
Cloud Security Implementation Services
Cloud security implementation services for enterprise-grade protection. Professional cloud security that protects data and ensures compliance.
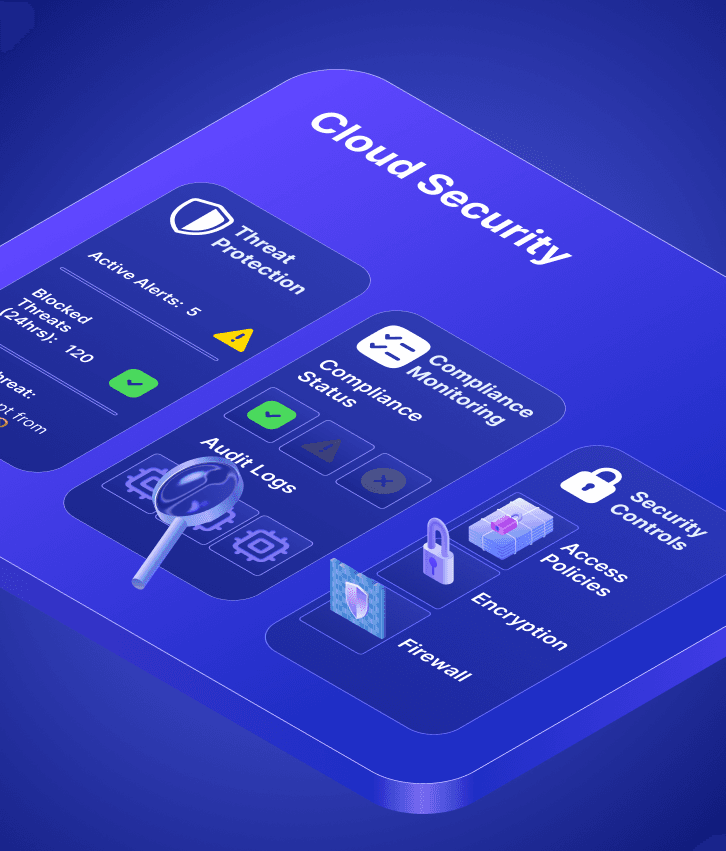
Enterprise-grade cloud security that protects your business data and ensures compliance without slowing down operations
Cloud security isn't optional—it's the foundation of business trust and regulatory compliance.
Most companies implement basic security that leaves them vulnerable to sophisticated attacks and compliance violations. Professional cloud security provides enterprise-level protection while enabling faster, more reliable operations.
From security gaps to fortress-level protection
Your cloud infrastructure has security vulnerabilities that could lead to data breaches and regulatory violations. Basic security configurations don't protect against advanced threats or meet compliance requirements. Security incidents disrupt business operations and damage customer trust. Meanwhile, companies with proper cloud security operate confidently knowing their data and operations are protected.
Inadequate security configurations that leave cloud infrastructure vulnerable to attacks
Compliance gaps that create regulatory risks and potential legal liabilities
Lack of threat monitoring and incident response capabilities for cloud environments
Inconsistent security policies across different cloud services and applications
Security measures that slow down development and business operations
Comprehensive security frameworks designed for cloud infrastructure protection
Secure user authentication and authorization across cloud resources
Advanced encryption and data security for sensitive information
Real-time monitoring and automated response to security threats
Security measures for GDPR, HIPAA, SOC 2, and industry-specific regulations
Our disciplined approach behind making the practical feel magical
Evaluate current cloud security posture and identify vulnerabilities
Create comprehensive security architecture for cloud infrastructure
Deploy security controls, monitoring, and protection systems
Verify security effectiveness through penetration testing and compliance audits
Ongoing security oversight with threat response and continuous improvement
Misconfigured clouds are breaches waiting to happen. We implement enterprise-grade security controls, monitoring, and compliance frameworks—so your business stays safe without slowing down.

Security Strategy, Built to Protect
Before implementing a single control, we help you assess cloud security posture, design comprehensive protection frameworks, and create security systems that defend without limiting agility. Whether you need strategic planning, complete implementation, or compliance support — we meet you where you are.

Comprehensive security planning and architecture design for cloud environments
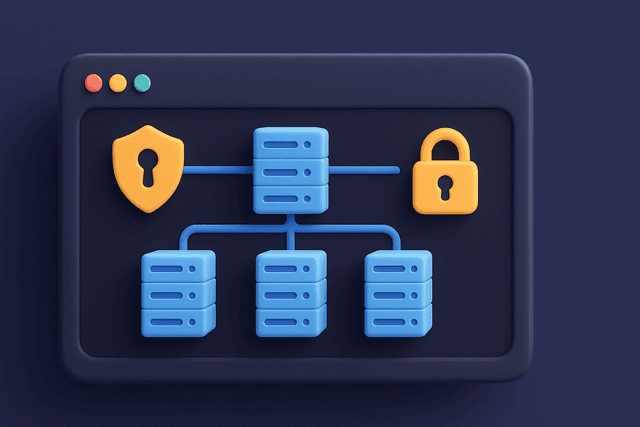
Complete deployment of cloud security controls and monitoring systems

Security measures and documentation for regulatory compliance requirements
Engage us for security audits or enterprise-grade cloud hardening.
Don’t gamble with your most valuable asset—your data. We design and implement cloud security architectures that stop threats, ensure compliance, and protect customer trust at scale.

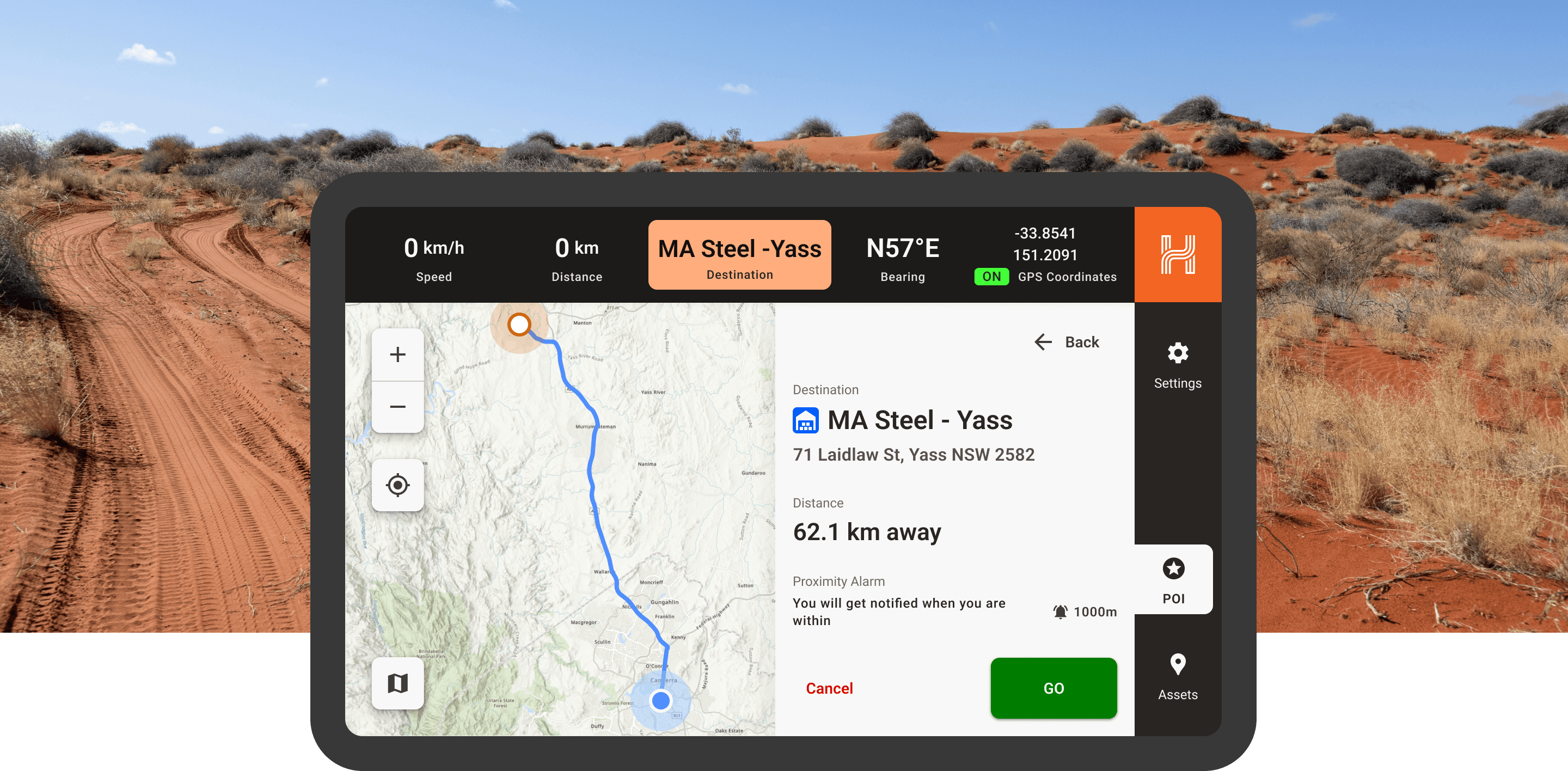
Case Study•
Built with Hema Maps, this rugged Android app powers navigation and asset tracking across remote Australia—even offline. Designed by White Widget.

News•
We’ve got some exciting news! Our website, White Widget (whitewidget.com), has won Gold in the Website Design category at the 8th Indigo Design Awards, and is shortlisted for Digital Design of the Year.