Assess Your Security Posture
Don’t wait for a breach to find your weak points. Our audits uncover hidden vulnerabilities, compliance gaps, and outdated policies—giving you a clear roadmap to stronger protection.
Security Audits & Risk Assessment Services
Security audits and risk assessment services for comprehensive threat evaluation. Professional cybersecurity analysis that identifies vulnerabilities before attackers do.
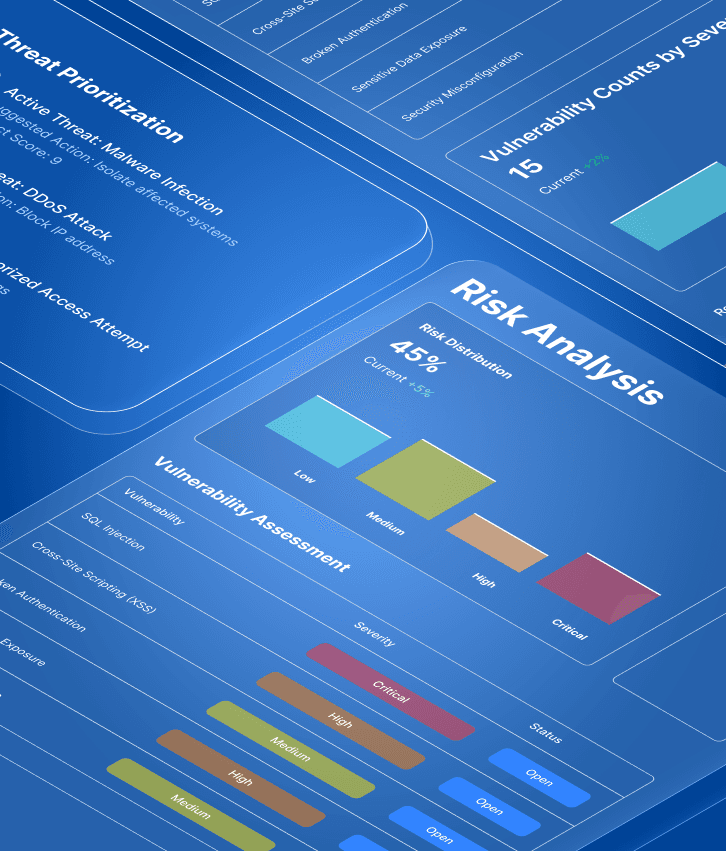
Comprehensive security audits that reveal hidden vulnerabilities and provide actionable roadmaps for protection
Most companies think they're secure until they're breached, but professional security audits reveal the gaps that hackers exploit.
You can't protect what you don't know is vulnerable. Our security assessments identify real risks and provide practical solutions that strengthen your defenses before attacks happen.
From false security to verified protection
Your organization has security vulnerabilities that you don't know about, creating risk of data breaches and regulatory violations. Current security measures give false confidence because they haven't been properly tested. Compliance auditors find gaps that create legal liabilities and customer trust issues. Meanwhile, companies with regular security audits are identifying and fixing vulnerabilities before they become expensive breaches.
Unknown security vulnerabilities that create hidden risks of data breaches and attacks
Compliance gaps that lead to regulatory violations and potential legal penalties
Outdated security policies that don't address current threats and business changes
Lack of security documentation required for insurance coverage and client contracts
False sense of security from untested controls that may fail during actual attacks
Full evaluation of technology, processes, and policies across all business systems
Detailed analysis of security weaknesses with business impact prioritization
Evaluation against regulatory requirements and industry standards
Assessment of current security policies and procedures for effectiveness
Evaluation of specific threats targeting your industry and business model
Our disciplined approach behind making the practical feel magical
Define assessment boundaries, objectives, and success criteria for security evaluation
Systematic evaluation of security controls, policies, and technology implementations
Identify vulnerabilities and rank them by business impact and likelihood
Compare current state to best practices and regulatory requirements
Provide actionable plan for addressing identified risks and improving security posture
Don’t wait for a breach to find your weak points. Our audits uncover hidden vulnerabilities, compliance gaps, and outdated policies—giving you a clear roadmap to stronger protection.

Security Strategy, Built to Assess
Before implementing a single control, we help you understand current vulnerabilities, prioritize risks, and create security roadmaps that provide comprehensive protection. Whether you need complete audits, ongoing assessments, or compliance support — we meet you where you are.

Comprehensive security assessment with detailed findings and recommendations

Ongoing security evaluation and risk management services
Specialized assessment for regulatory compliance and certification requirements
We flex from lightweight audits to enterprise risk assessments for compliance.
Security isn’t about assumptions—it’s about proof. Our audits and risk assessments deliver verified protection, compliance readiness, and peace of mind against evolving threats.


Article•
Explore how Digital Twins are transforming smart transportation through predictive maintenance, AI integration, and vendor-neutral system design; powered by semantic modeling and knowledge graphs.
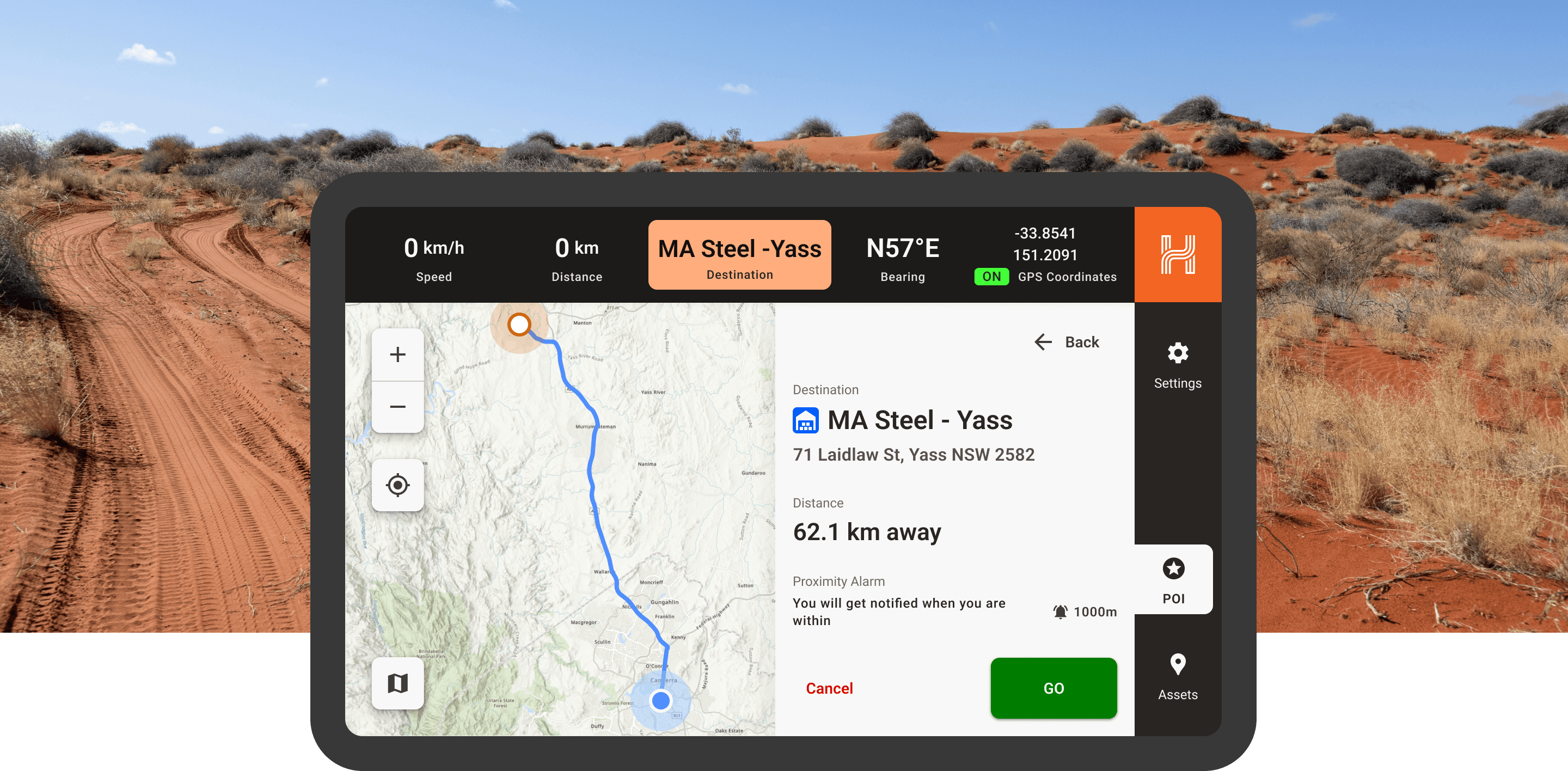
Case Study•
Built with Hema Maps, this rugged Android app powers navigation and asset tracking across remote Australia—even offline. Designed by White Widget.