Secure Your Systems
Don’t wait for a breach to find out where you’re vulnerable. We implement layered defenses, compliance-ready safeguards, and real-time monitoring to keep your business safe.
Web Security Implementation
Web security implementation for enterprise-grade protection. Website security services that protect business and customer data from threats.

Enterprise-grade security that protects your business and customer data from threats
Security breaches don't just cost money—they destroy trust and can shut down your business overnight.
Most companies think they're secure until they're not, and by then it's too late. We implement layered security that protects against real threats without making your site impossible to use.
From vulnerability to protection
Your website is vulnerable to attacks because security wasn't built in from the start. Customer data isn't properly protected, creating compliance risks. Your team doesn't know how to identify or respond to security threats. Meanwhile, cybercriminals are constantly finding new ways to exploit vulnerable websites.
Vulnerable websites that lack proper security measures and monitoring
Inadequate data protection that puts customer information at risk
Poor authentication systems that allow unauthorized access
Lack of security monitoring and incident response capabilities
Compliance gaps that create legal and regulatory risks
Comprehensive evaluation of current security posture
Encrypted communication and secure data transmission
Secure user management and permission systems
Continuous security monitoring and incident management
Security measures for GDPR, CCPA, and industry regulations
Our disciplined approach behind making the practical feel magical
Identify vulnerabilities and security gaps in existing systems
Prioritize security improvements based on business impact and threat likelihood
Deploy comprehensive security measures and monitoring systems
Verify security effectiveness through penetration testing and audits
Ongoing security oversight and threat response capabilities
Don’t wait for a breach to find out where you’re vulnerable. We implement layered defenses, compliance-ready safeguards, and real-time monitoring to keep your business safe.

Security Strategy, Built to Defend
Before implementing a single control, we help you assess current vulnerabilities, plan comprehensive protection, and create security systems that defend without disrupting operations. Whether you need strategic consulting, complete implementation, or ongoing management — we meet you where you are.
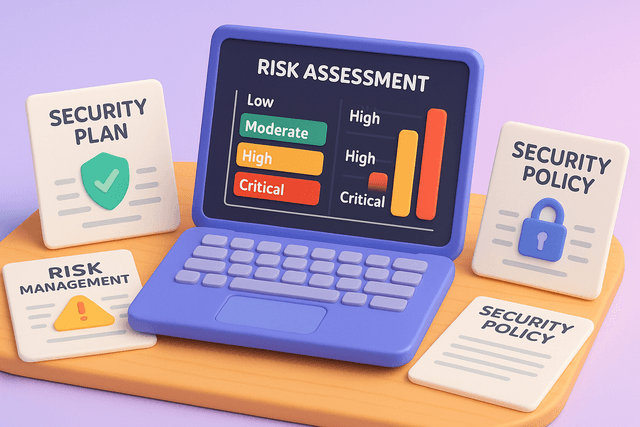
Comprehensive security planning and risk assessment
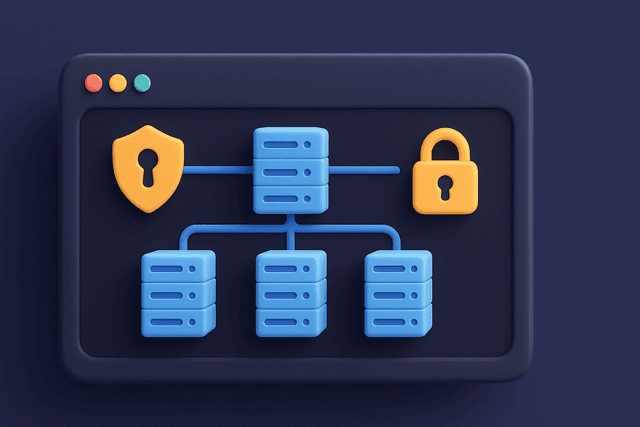
Complete security system deployment and configuration

Continuous monitoring and threat response services
We support anything from quick audits to enterprise security hardening.
Security isn’t optional—it’s survival. We design and deploy enterprise-grade protections that safeguard your data, customers, and reputation while meeting regulatory standards. Let’s build a defense that evolves as fast as the threats.


Article•
Explore how Digital Twins are transforming smart transportation through predictive maintenance, AI integration, and vendor-neutral system design; powered by semantic modeling and knowledge graphs.
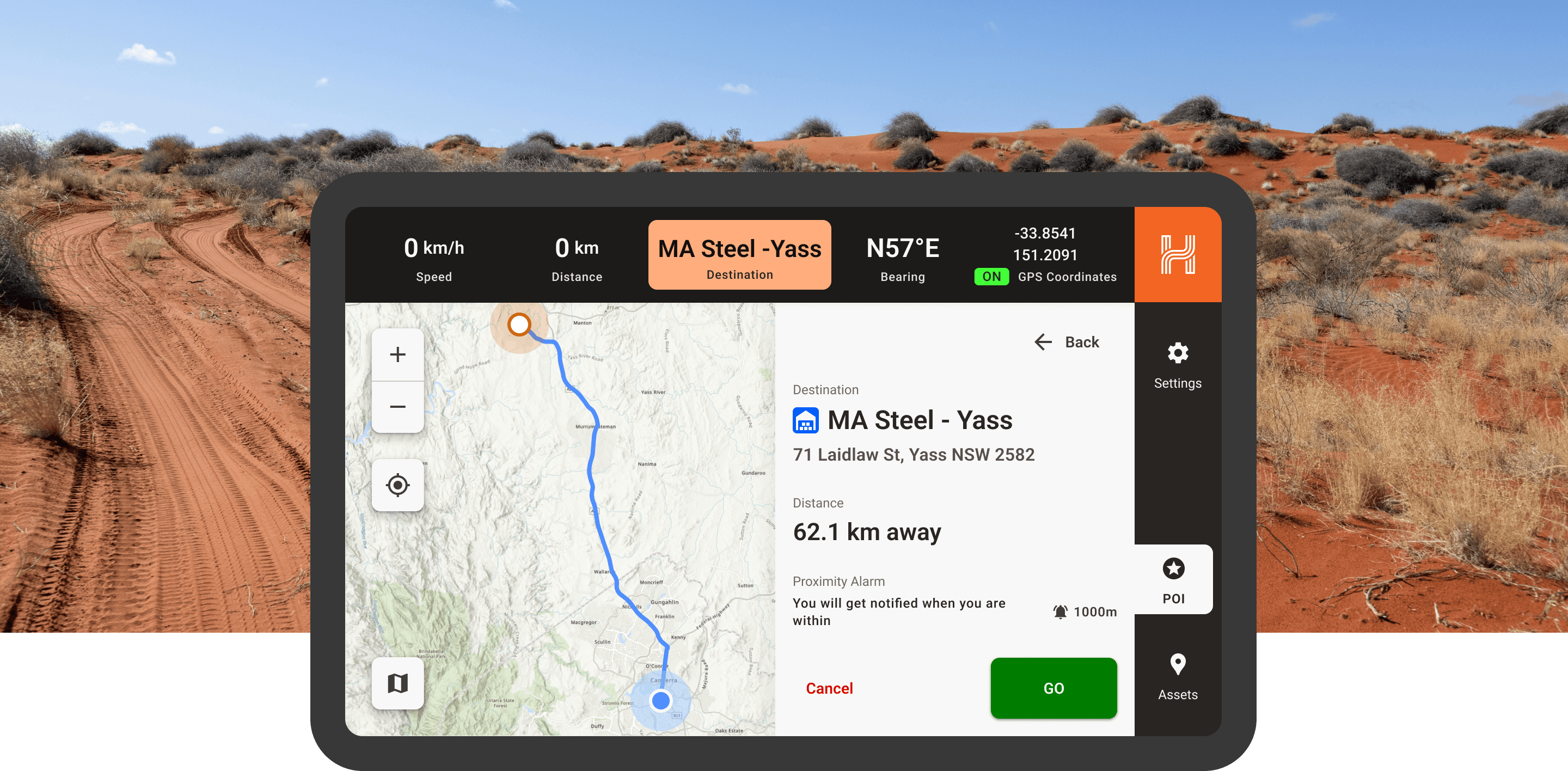
Case Study•
Built with Hema Maps, this rugged Android app powers navigation and asset tracking across remote Australia—even offline. Designed by White Widget.