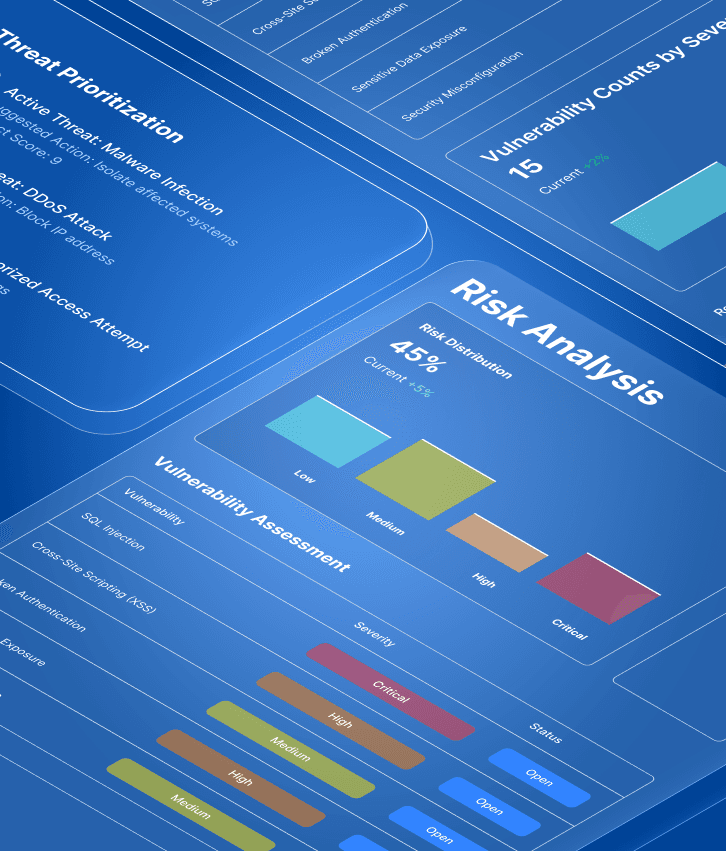
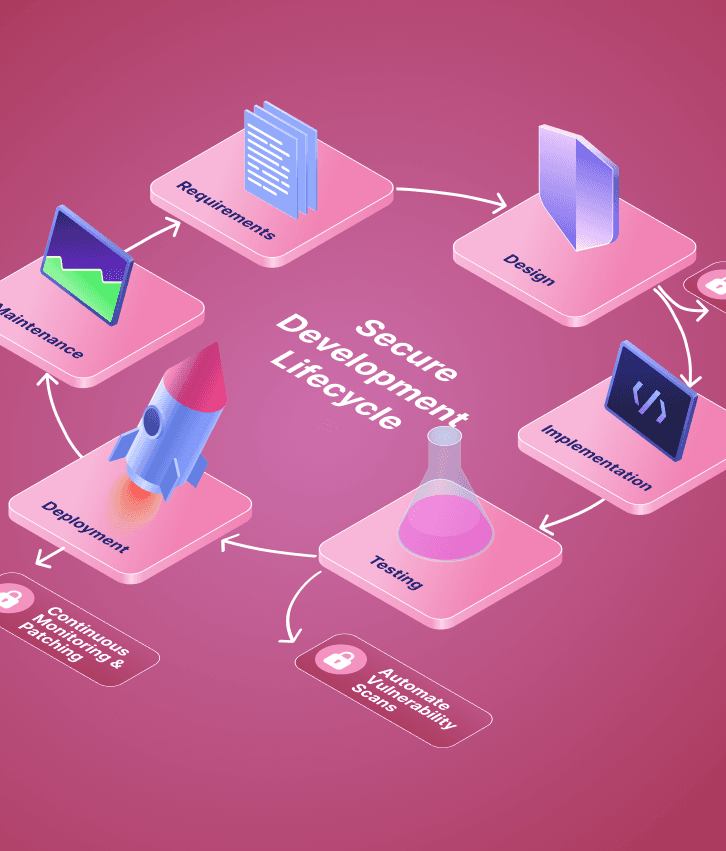
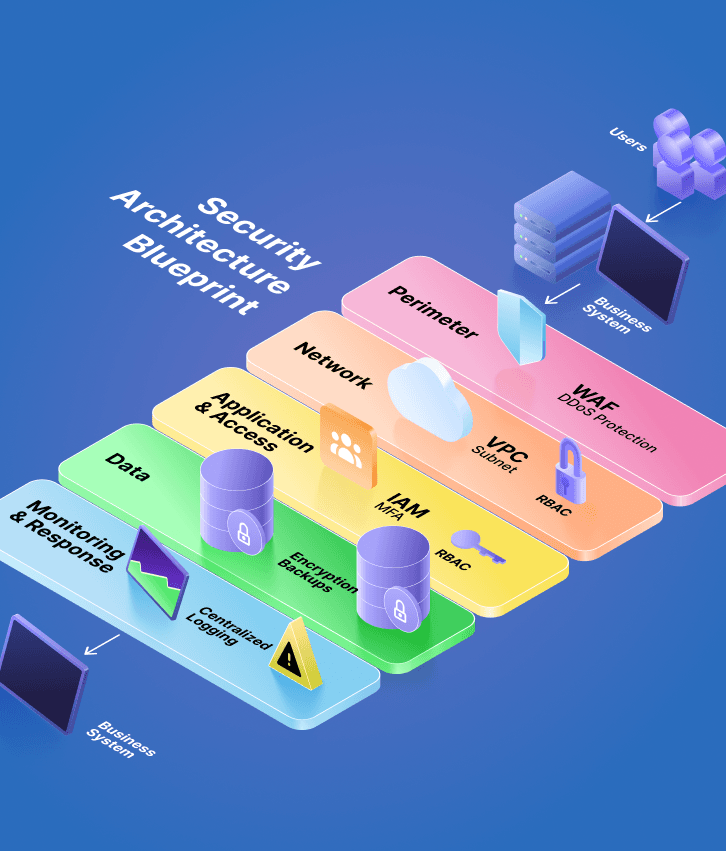
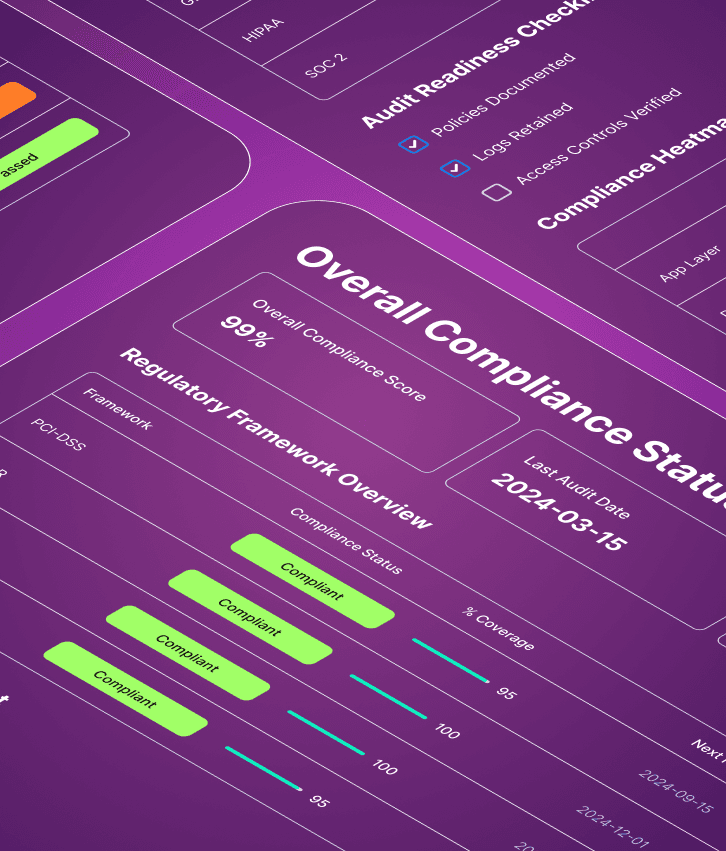
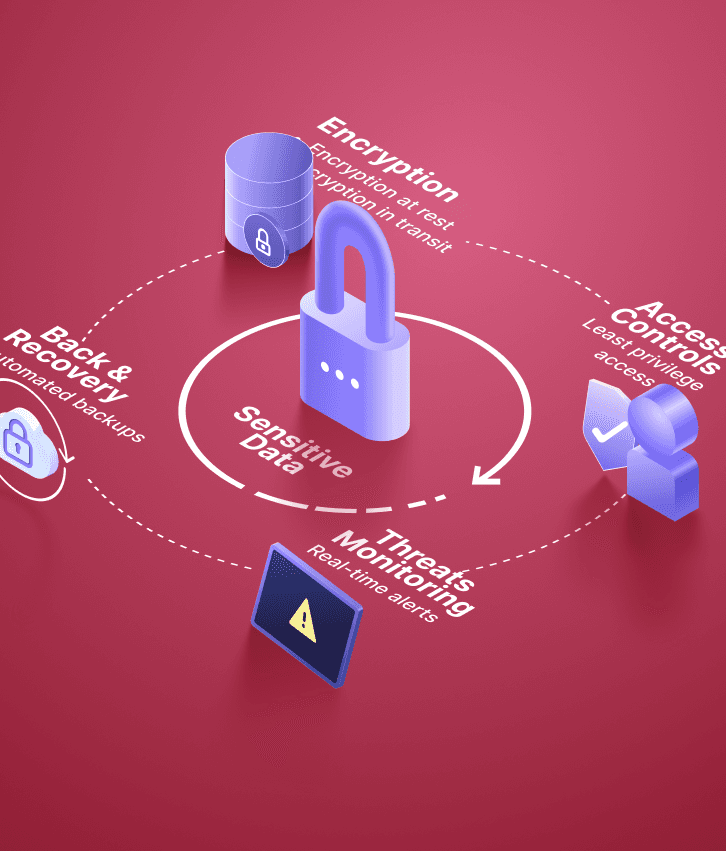
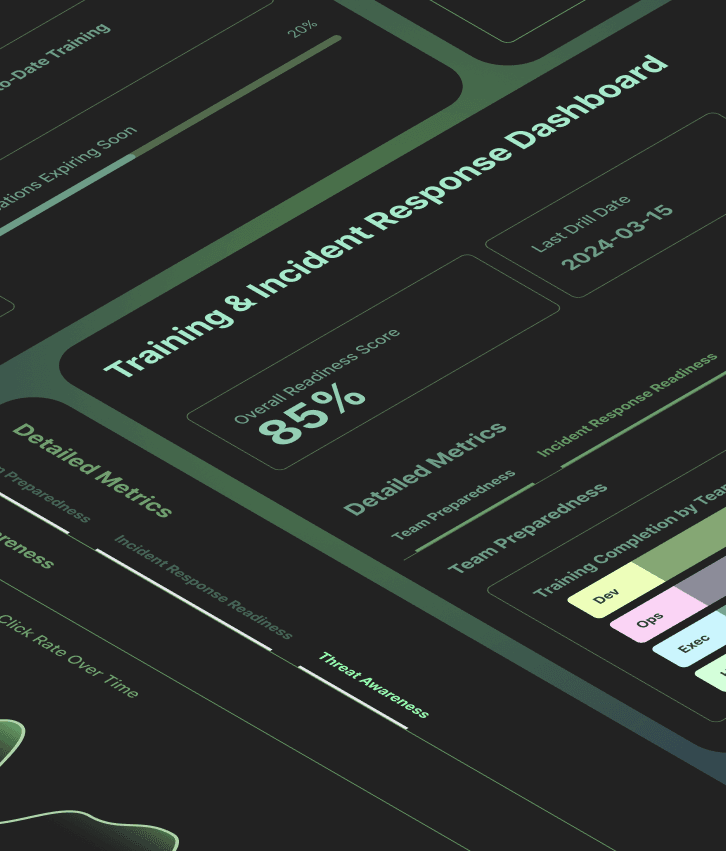
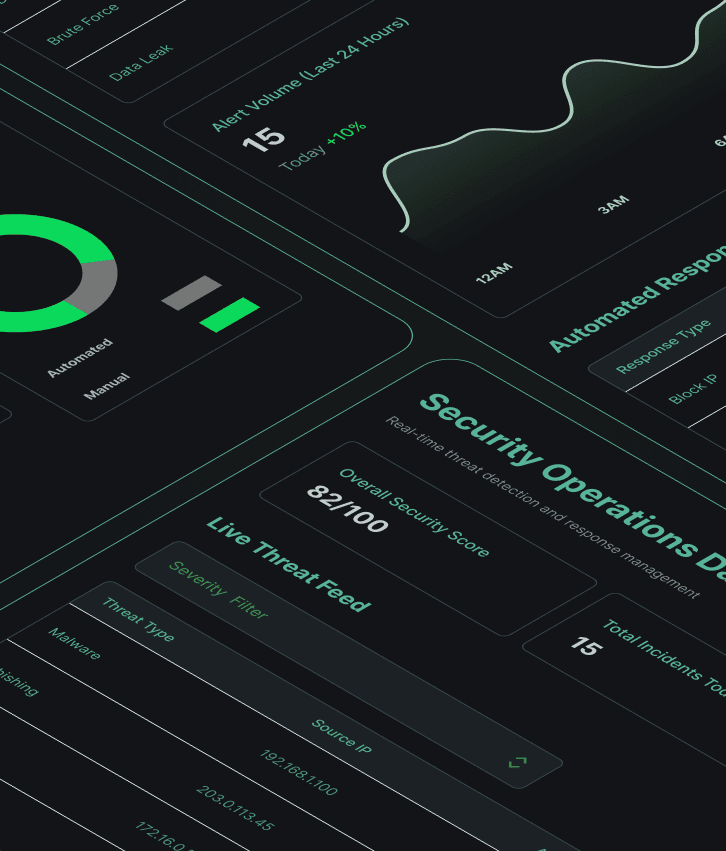
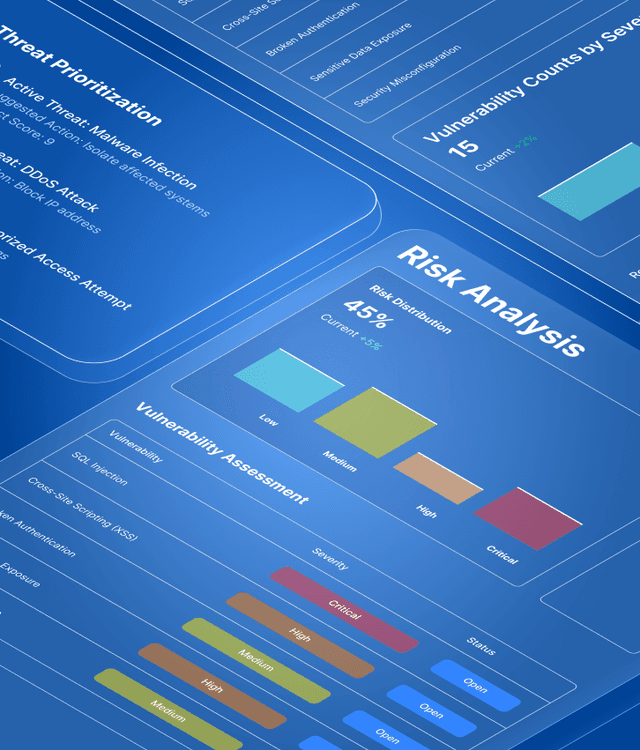
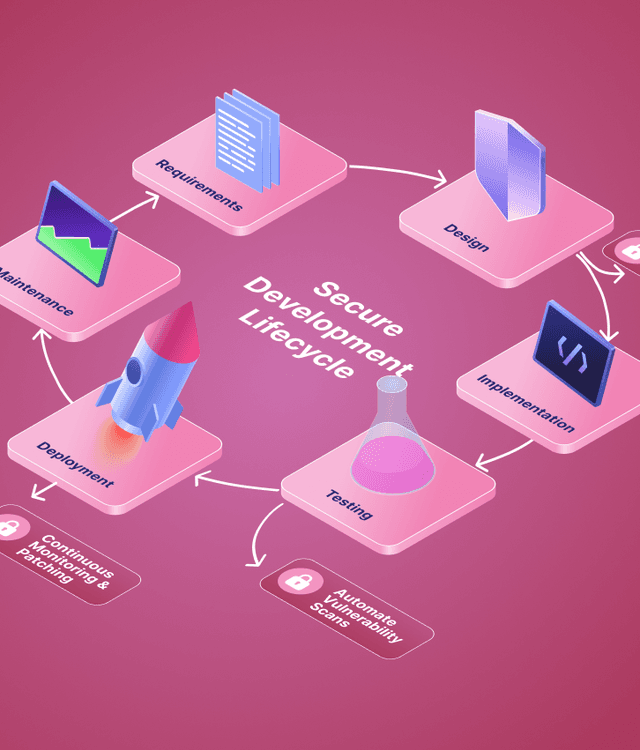
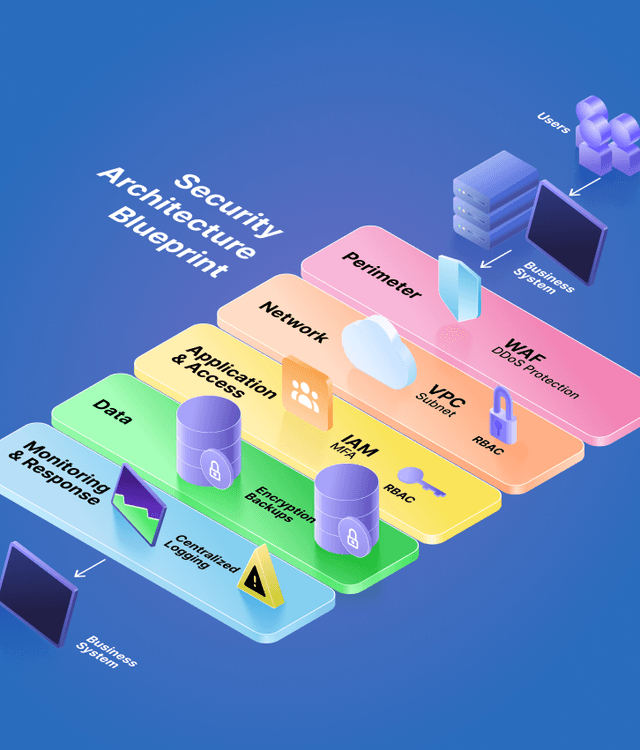
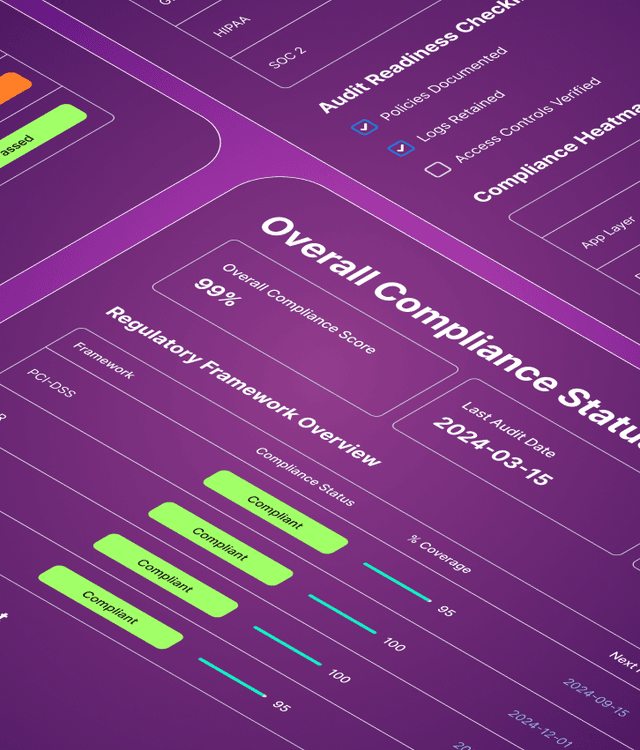
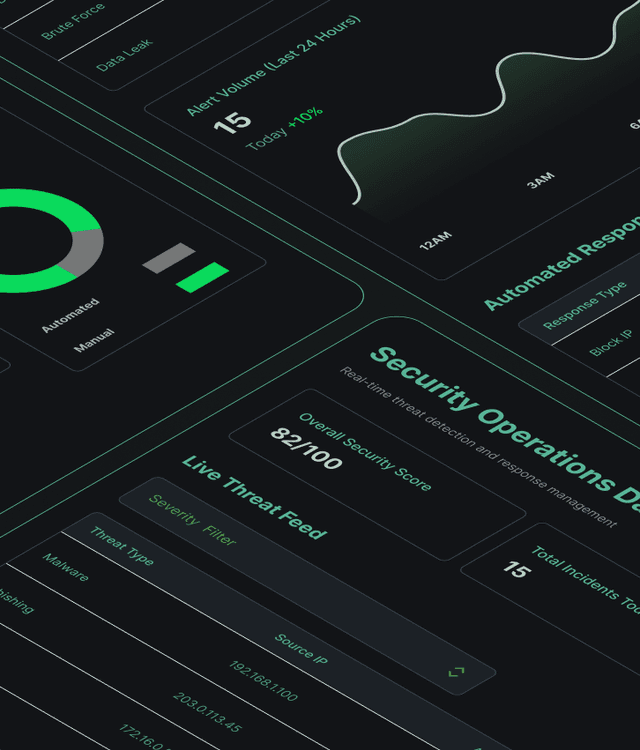
Build security that protects everything that matters
Most security creates friction that slows business operations. We engineer security frameworks that enhance productivity while stopping threats. Protection that adapts to your business, not the other way around.