Develop Secure Software
Don’t wait for a breach to test your code. We embed security into every stage of development—so your applications launch faster, stay compliant, and resist real-world attacks.
Secure Software Development Services
Secure software development services for vulnerability-free applications. Security-first development that prevents breaches and protects business data.
Security-first software development that builds protection into every line of code from day one
Most software is built with security as an afterthought, creating vulnerabilities that hackers exploit for years.
Fixing security issues after development costs 100 times more than building it right from the start. Secure development practices create software that resists attacks and protects your business and customers.
From vulnerable code to bulletproof software
Your applications contain security vulnerabilities that expose business and customer data to theft and manipulation. Security issues discovered after launch require expensive emergency fixes that disrupt operations. Customers lose trust when security breaches expose their personal information. Meanwhile, companies with secure development practices are building software that resists attacks and maintains customer confidence.
Security vulnerabilities built into applications that create ongoing risk of data breaches
Expensive security fixes required after software deployment that could have been prevented
Compliance failures from applications that don't meet regulatory security requirements
Customer trust issues when security breaches expose personal or business information
Competitive disadvantages from security reputation problems and compliance delays
Security planning and threat modeling during application design phase
Development techniques that prevent common vulnerabilities and attack vectors
Expert analysis of application code for security weaknesses and improvements
Comprehensive testing for security vulnerabilities throughout development
Automated security validation and secure application deployment processes
Our disciplined approach behind making the practical feel magical
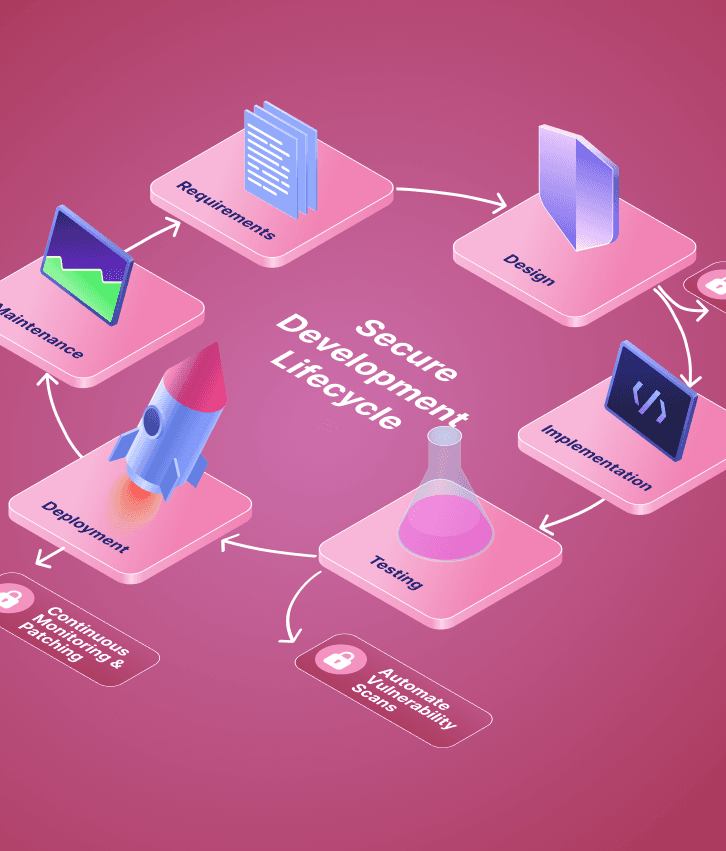
Identify security requirements and potential threats during design phase
Create application architecture that incorporates security best practices
Build applications using security-focused coding practices and frameworks
Comprehensive testing for vulnerabilities and security effectiveness
Deploy applications with security controls and ongoing security monitoring
Don’t wait for a breach to test your code. We embed security into every stage of development—so your applications launch faster, stay compliant, and resist real-world attacks.

Development Strategy, Built to Secure
Before writing a single line of code, we help you integrate security requirements, plan secure architectures, and create development practices that prevent vulnerabilities from day one. Whether you need strategic consulting, complete development, or security reviews — we meet you where you are.

Security guidance and best practices for development teams

Complete secure software development from design to deployment

Security assessment and improvement of existing development processes
Engage us for advisory, code reviews, or full secure SDLC implementation.
Security shouldn’t be an afterthought. With secure coding, code reviews, and built-in compliance, we help you deliver software that customers trust and attackers can’t exploit.

Article•
Choosing between native or cross-platform in 2025? Learn which mobile development strategy scales best for performance, cost, and long-term ROI.

Case Study•
Milk & Honey is the Philippines' cutest boutique baby needs site, and we launched Android and iOS apps for them in record time, using our platform Trailblaze.