Architect Your Security Future
Stop patching gaps with one-off tools. We design unified security architectures—zero trust, layered defenses, and integrated controls—that protect your business without slowing it down.
Security Architecture Design Services
Security architecture design services for comprehensive protection frameworks. Enterprise security design that protects business operations and customer data.
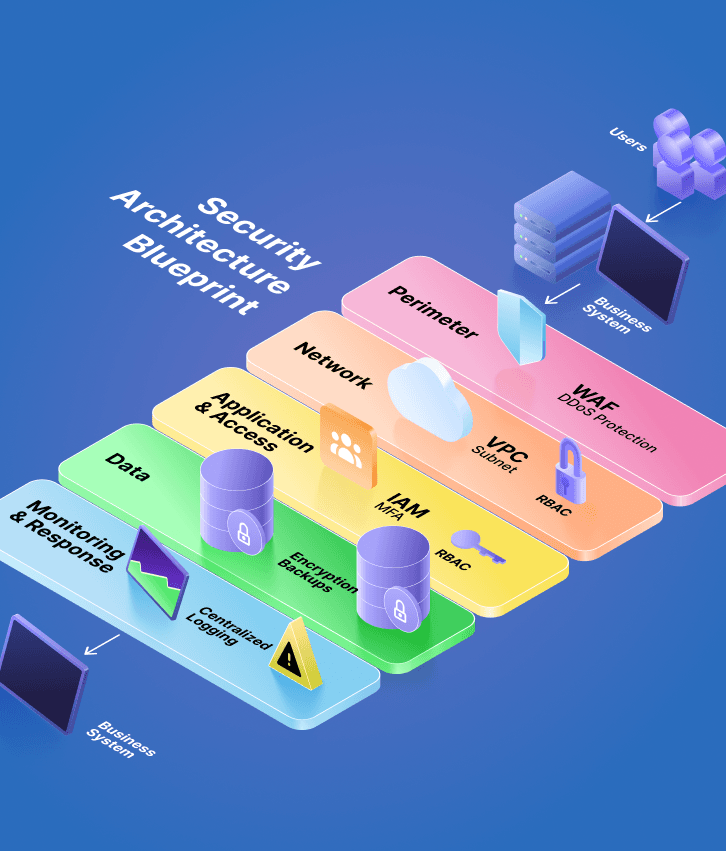
Enterprise security architecture that creates comprehensive, layered protection for your entire business operation
Piecemeal security solutions leave gaps that attackers exploit, but comprehensive security architecture creates overlapping protection that stops threats at multiple levels.
Your business needs security design that protects everything from customer data to business operations while enabling productivity and growth.
From security gaps to fortress-level architecture
Your current security approach has gaps between different systems and solutions that attackers exploit to access sensitive data. Security technologies don't work together effectively, creating blind spots and management complexity. Business operations are disrupted by security measures that weren't designed for your workflows. Meanwhile, companies with proper security architecture enjoy comprehensive protection that enhances rather than hinders business operations.
Fragmented security solutions that leave gaps between different systems and technologies
Security measures that disrupt business operations because they weren't designed holistically
Lack of comprehensive protection strategy that addresses all business risks and threats
Expensive security technologies that don't integrate effectively or provide complete coverage
Compliance challenges from security architectures that don't meet regulatory requirements
Comprehensive security architecture spanning all business systems and operations
Security design that verifies every access request regardless of location or user
Layered security controls that provide multiple protection levels
Comprehensive user authentication and authorization architecture
Architecture that integrates security seamlessly with business operations
Our disciplined approach behind making the practical feel magical
Understand business operations, data flows, and relevant threat landscape
Identify comprehensive security needs including compliance and business requirements
Create detailed security architecture with integrated protection layers
Develop phased deployment plan for security architecture components
Test architecture effectiveness and optimize for business operations and security
Stop patching gaps with one-off tools. We design unified security architectures—zero trust, layered defenses, and integrated controls—that protect your business without slowing it down.

Security Strategy, Built to Fortify
Before implementing a single security control, we help you design comprehensive frameworks, plan layered defenses, and create security architectures that protect everything without hindering operations. Whether you need strategic consulting, complete design, or modernization services — we meet you where you are.

Comprehensive security framework design and implementation planning
Complete security architecture development for organization-wide protection
Architecture updates that improve protection while enhancing business operations
From threat models to enterprise security architecture, we flex engagement depth.
From customer data to core operations, your entire business deserves protection. With enterprise-grade architecture, we create a security framework that closes gaps, meets compliance, and grows with you.


Article•
Explore how Digital Twins are transforming smart transportation through predictive maintenance, AI integration, and vendor-neutral system design; powered by semantic modeling and knowledge graphs.
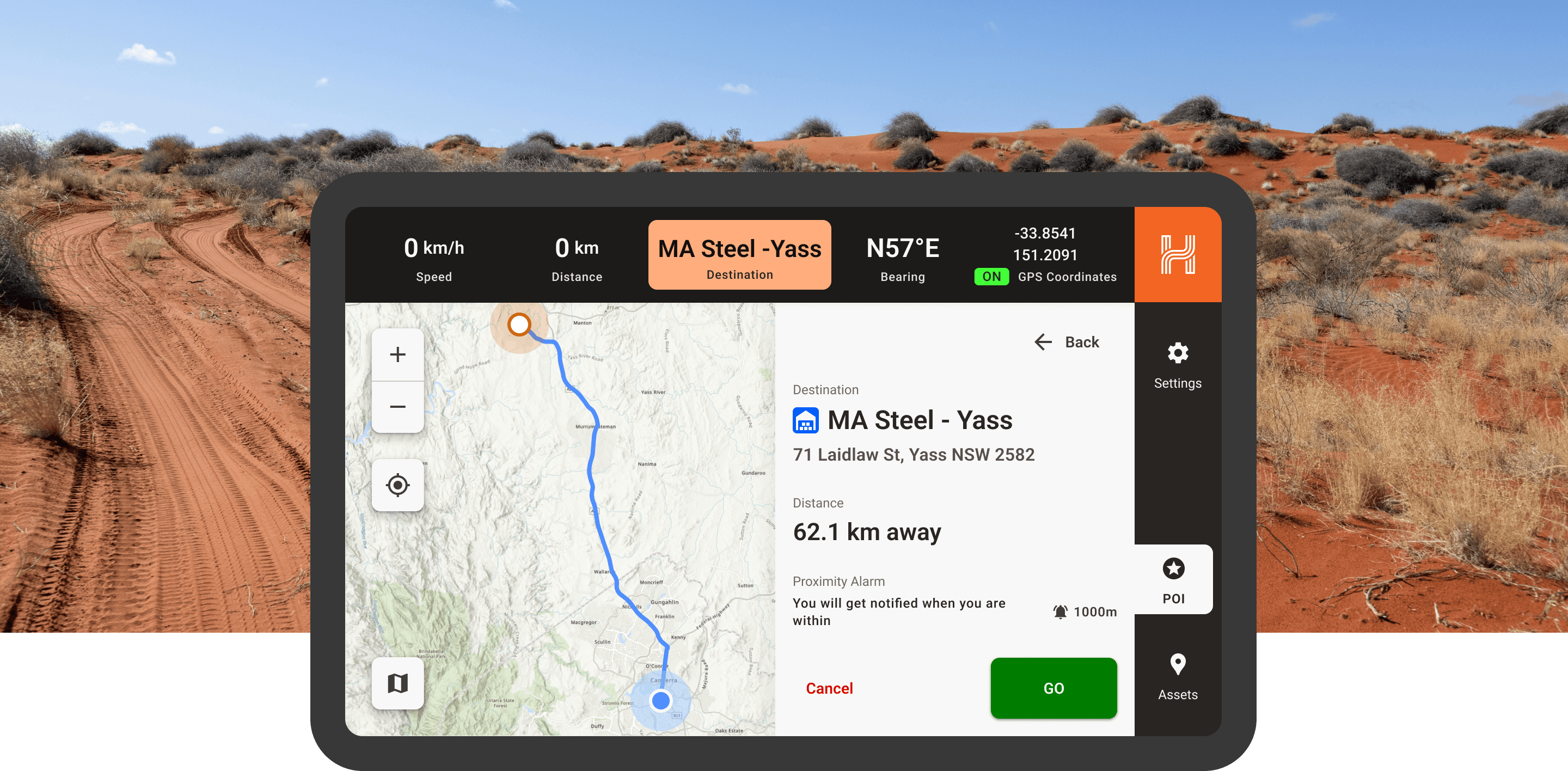
Case Study•
Built with Hema Maps, this rugged Android app powers navigation and asset tracking across remote Australia—even offline. Designed by White Widget.