Start Continuous Protection
Cyber threats don’t wait for business hours—and neither should your defenses. Our 24/7 monitoring detects threats the moment they appear and responds instantly, keeping your business safe around the clock.
Security Monitoring Services
Security monitoring services for continuous threat detection. 24/7 cybersecurity monitoring that identifies and responds to threats in real-time.
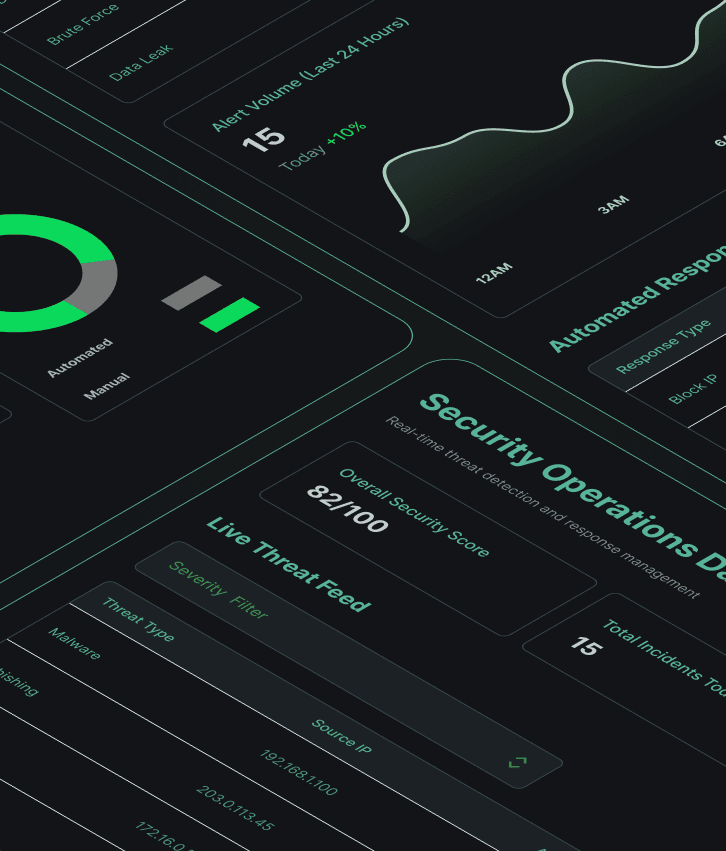
24/7 security monitoring that detects and responds to threats before they become data breaches
Cyber attacks happen 24/7, but most companies only monitor security during business hours.
By the time you discover a breach, attackers have been in your systems for months stealing data and causing damage. Continuous security monitoring catches threats immediately and responds automatically to protect your business.
From security blindness to total visibility
Security threats go undetected for months because your organization lacks continuous monitoring and threat detection capabilities. When attacks are finally discovered, the damage is already extensive and expensive to remediate. Manual security monitoring misses sophisticated threats that evolve faster than human analysis. Meanwhile, companies with professional security monitoring are detecting and stopping attacks in minutes instead of months.
Undetected security threats that operate in systems for extended periods causing extensive damage
Limited security monitoring that only covers business hours when attacks happen around the clock
Overwhelming security alerts that create noise without actionable threat intelligence
Slow threat response that allows attackers to achieve objectives before detection and containment
Lack of security expertise to properly analyze threats and coordinate effective responses
Continuous monitoring with real-time threat identification and alert generation
Immediate threat containment and response coordination during security incidents
Expert analysis of security threats with context and business impact assessment
Automated threat containment and response systems for immediate protection
Comprehensive security monitoring with expert analyst support and coordination
Our disciplined approach behind making the practical feel magical
Deploy comprehensive security monitoring across all systems and networks
Configure automated threat detection with customized rules and intelligence feeds
Create incident response procedures with escalation and containment protocols
Begin continuous monitoring with expert analyst support and response capabilities
Regular monitoring optimization with threat landscape updates and procedure refinements
Cyber threats don’t wait for business hours—and neither should your defenses. Our 24/7 monitoring detects threats the moment they appear and responds instantly, keeping your business safe around the clock.

Security Strategy, Built to Watch
Before detecting a single threat, we help you plan comprehensive monitoring, design response procedures, and create 24/7 security operations that catch attacks before they cause damage. Whether you need managed monitoring, complete SOC services, or hybrid solutions — we meet you where you are.

Complete 24/7 security monitoring with expert analysis and response coordination
Comprehensive security monitoring and incident response with dedicated analyst support

Combined automated monitoring with periodic expert review and response support
From lightweight monitoring pilots to 24/7 enterprise coverage, we fit the model.
Don’t give attackers months of free access—catch them in minutes. With always-on monitoring, automated response, and expert analysts, your business stays protected no matter when or how threats strike.


Article•
Explore how Digital Twins are transforming smart transportation through predictive maintenance, AI integration, and vendor-neutral system design; powered by semantic modeling and knowledge graphs.
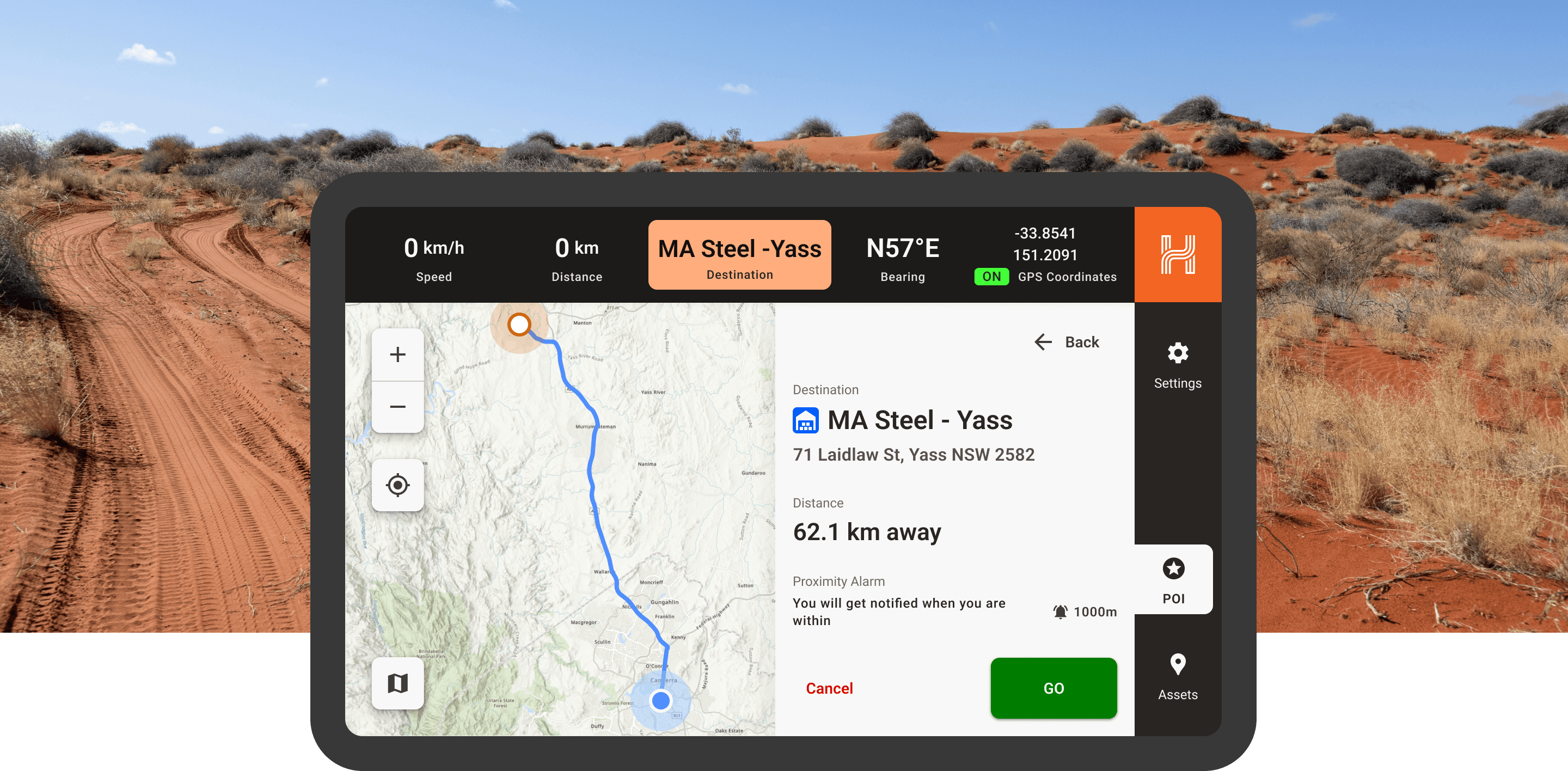
Case Study•
Built with Hema Maps, this rugged Android app powers navigation and asset tracking across remote Australia—even offline. Designed by White Widget.