Secure Your Data Assets
Data is your most valuable business resource—don’t leave it exposed. Our solutions classify, encrypt, and safeguard sensitive information while ensuring compliance and business continuity.
Data Protection Solutions Services
Data protection solutions for comprehensive information security. Enterprise data protection that safeguards business and customer information from threats.
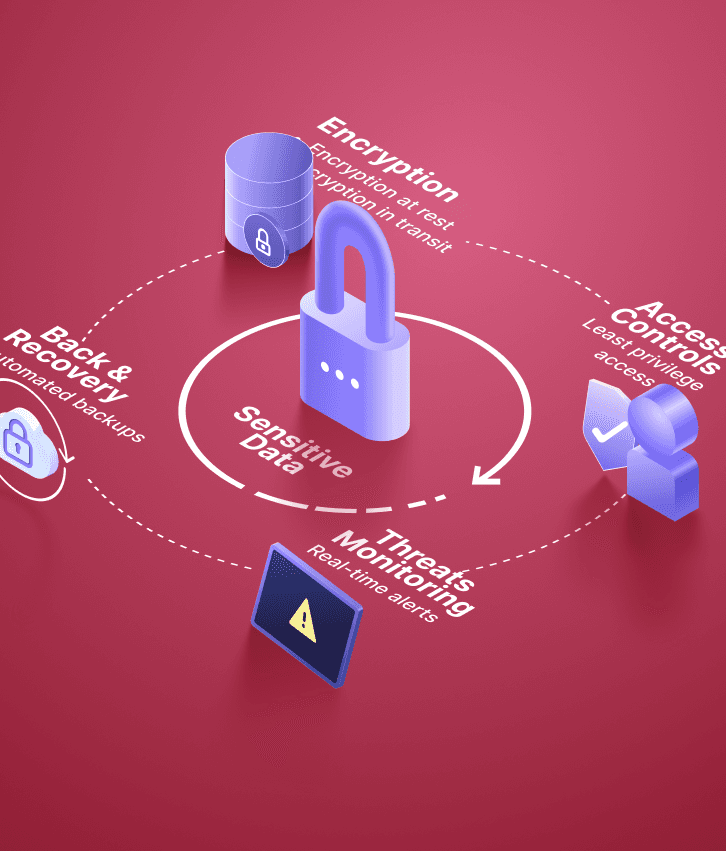
Comprehensive data protection that safeguards your business information and customer data from theft, loss, and unauthorized access
Your data is your most valuable business asset, but most companies don't protect it properly until after a breach.
Data protection isn't just about compliance—it's about protecting the information that runs your business and maintaining customer trust. Comprehensive data protection prevents breaches, ensures business continuity, and protects your competitive advantages.
From data vulnerability to information fortress
Your business and customer data is vulnerable to theft, loss, and unauthorized access that could destroy your company. Data breaches result in massive financial penalties, legal liabilities, and permanent damage to customer trust. Inadequate data protection creates compliance violations and business disruptions. Meanwhile, companies with proper data protection are confidently handling sensitive information while maintaining customer trust and competitive advantages.
Business and customer data vulnerable to theft, unauthorized access, and malicious attacks
Inadequate data backup and recovery capabilities that risk permanent information loss
Poor data classification and handling that creates compliance violations and security gaps
Lack of data encryption that exposes sensitive information during transmission and storage
Insufficient access controls that allow unauthorized personnel to access confidential information
Systematic identification and management of sensitive information assets
Advanced encryption and protection for data at rest and in transit
Comprehensive user authentication and data access management
Reliable data backup and recovery capabilities for business continuity
Automated systems that prevent unauthorized data access and transmission
Our disciplined approach behind making the practical feel magical
Identify and categorize all business data by sensitivity and protection requirements
Evaluate data vulnerabilities and design comprehensive protection strategies
Deploy encryption, access controls, and protection systems for identified data assets
Implement reliable data backup and recovery capabilities for business continuity
Ongoing data protection monitoring with compliance validation and improvement
Data is your most valuable business resource—don’t leave it exposed. Our solutions classify, encrypt, and safeguard sensitive information while ensuring compliance and business continuity.

Data Strategy, Built to Protect
Before implementing a single control, we help you classify sensitive data, assess protection needs, and create comprehensive solutions that safeguard your most valuable business assets. Whether you need strategic planning, complete implementation, or ongoing governance — we meet you where you are.

Comprehensive data protection planning and framework development

Complete deployment of data protection systems and controls

Ongoing data protection management with regulatory compliance support
From targeted encryption rollouts to enterprise-wide data protection, we adapt to need.
Breaches cost millions and destroy trust. With enterprise-grade encryption, access controls, and recovery systems, we turn your data from a liability into a strength. Protect your business, your customers, and your future.


Article•
Explore how Digital Twins are transforming smart transportation through predictive maintenance, AI integration, and vendor-neutral system design; powered by semantic modeling and knowledge graphs.
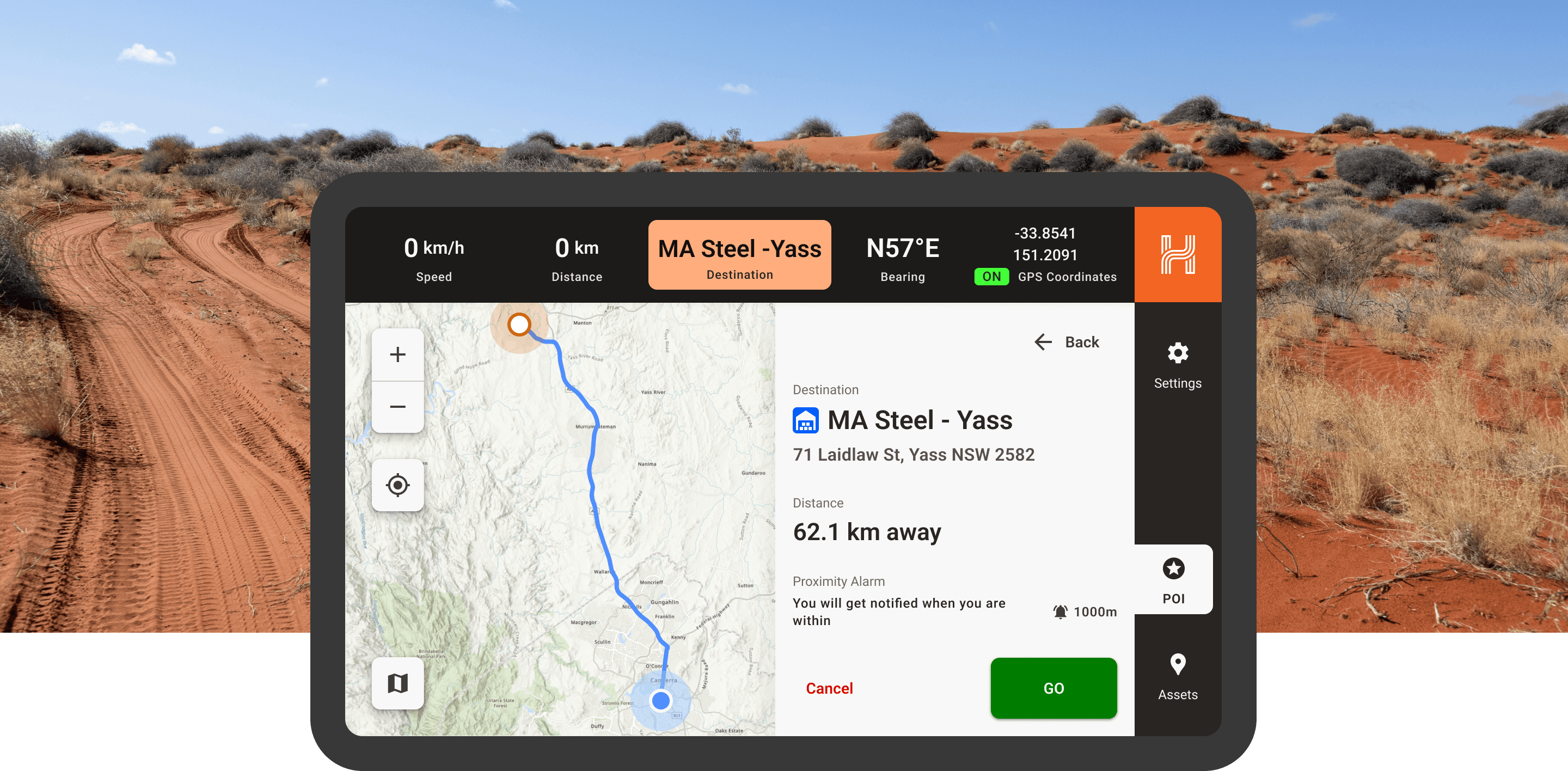
Case Study•
Built with Hema Maps, this rugged Android app powers navigation and asset tracking across remote Australia—even offline. Designed by White Widget.